Account Lockout Threshold is a feature in Windows 11 that, at the time of writing this article, is only available in Windows XNUMX. insider preview version. It is expected that the “Account Lockout Threshold” policy will be added to the release version.
If you enable this “Account Lockout Threshold” policy, any remote or local mis-login will automatically lock out the user account for a set period of time. It is one of the new security features that Microsoft has added in Windows 11 to prevent attacks on computer systems.
Account Lockout Threshold is a feature you can enable through local group policy. This feature is not available by default in Windows 11 home, but you can add it.
Enabling this “Account Lockout Threshold” security setting determines the number of failed login attempts before a user account is locked out. A locked account cannot be used until it has been reset by an administrator or the account lockout period has expired. You can set a value between 0 and 999 for the number of failed login attempts. If you set the value to 0, the account will never be locked.
Failed login attempts on workstations or member servers locked with Ctrl+Alt+Del or a screen saver with password also count towards this setting.
Change account lockout threshold in Windows 11
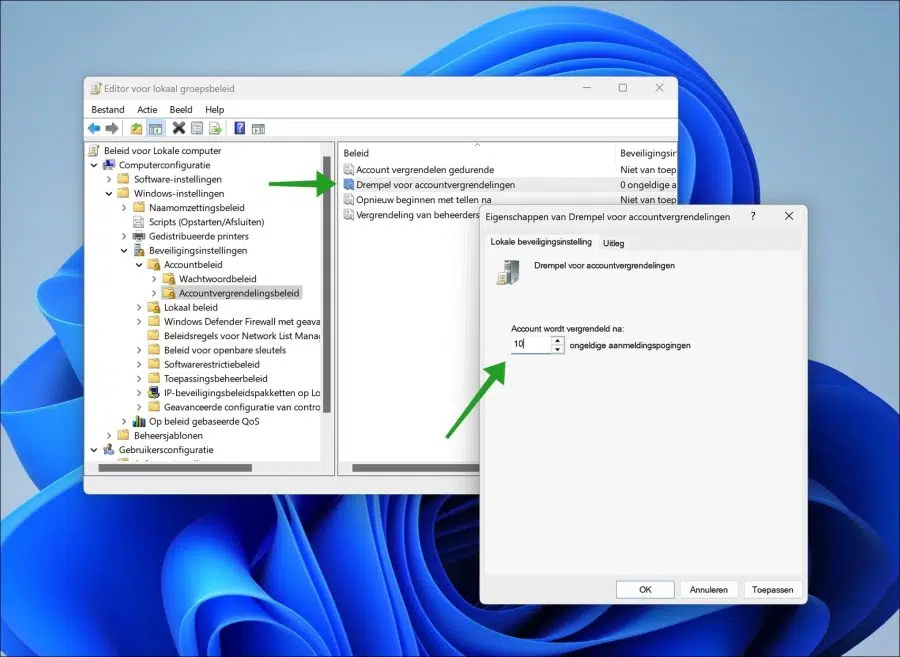
To activate this feature, open the local group policy. Right-click on the Start button. In the menu click on Run. In the run window type: gpedit.msc
On the left, click “Computer Configuration”, “Windows Settings”, then “Security Settings”, “Account Policies” and open “Account Lockout Policy”.
Double-click “Account Lockout Threshold” to change the policy value. You can now enter the number of failed login attempts after which the account will be locked.
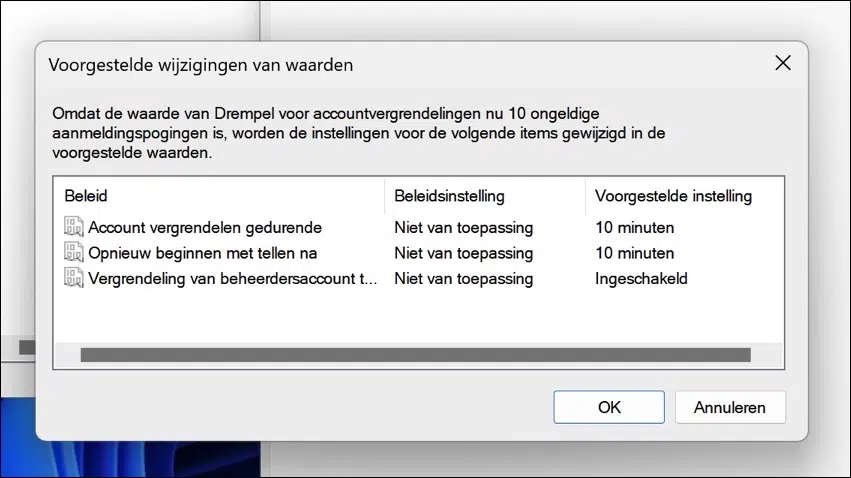
If you enable this policy by specifying a value of “1” or more, other policy settings will also become active. These policy settings support this policy.
This concerns the following policy settings that are given default policy values.
- Lock account for.
- Start counting again after.
- Allow administrator account lockout.
You can see the suggested settings for this policy in the images below. You can also adjust these.
You can enable this policy on a home PC or a work PC. The advantage of this policy is that if a computer in the network is taken over by attackers, attackers often try to advance in a network. Attackers do this by attacking different user accounts by constantly entering a different password until the actual password is cracked. This is then logged in and the attack starts again. This technique is called “brute force”, and it is used to take over as many computers as possible in the network.
By applying this “account lockout threshold” policy you can make the attack much more difficult. Every time an incorrect password is entered for the X number of times you set, the account will be locked for 10 minutes. This makes it a bit more difficult for an attacker to spread through the network.
I hope to have informed you with this. Thank you for reading!